This is an old revision of the document!
- title:
- rfid door lock
- members:
- zediek, loreto, carl.simpao, dolf
- skills:
- electronics, arduino
- status:
- in_progress
Introduction
Ryan from a small BPO in Dumaguete asked Project NightOwl, a technology incubator and hacker space at Foundation University, Dumaguete, to develop an RFID-based authentication and authorization method for a single door to their data center. Since NightOwl already started doing this for their own lab, extending it to a BPO where the internet infrastructure is already provisioned by Foundation University, is feasible. This is an ideal project for NightOwl to take on, since it involves R&D and prototyping based on knowledge and experience already partially obtained. It also provides the students of FU with an ideal opportunity to get working experience in a product development project for a real client, including the whole project management, quality control and documentation process. Lastly, the client is very interested in the concept of the NightOwl incubator/hacker-space and is happy to support it by providing some additional budget that can be used to buy additional tools/materials for NightOwl.
Since this project will be used in functioning company where security is essential, the quality standards of this project must be much higher than would be allowed internally at NightOwl. Details are important and bugs should be solved promptly. Code quality and security are important aspects.
Client requirements:
- Open Source as much as possible
- Secure
- Use same ID cards as FU
Project Scope and Requirements
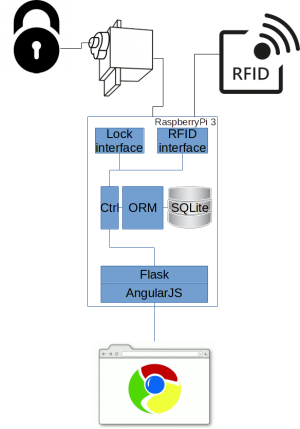
The overall goal is to provide a secure, easy to use and extensible integrated system of hardware and software for a locking mechanism, RFID based authentication, database based authorization and a web-based management application of these components, including an auditing trail. The system should be built securely to prevent un-authorized access and tampering, and be extensible so additions to the software and hardware may be made later on, both for that location, and for other locations.
Software
- Use existing open source software as much as we can
- Devise a plan for security updates of the used software
- A secure and simple webapplication is needed that provides:
- Authentication management (register and remove ID's)
- Authorization management (record which users are allowed to do what)
- Audit trail (show who accessed which resources when)
- Employ rigid testing and CI practices to ensure code quality
- Ensure user's privacy by not providing any information about cards and users to unauthorized user
- Regular backups
Hardware
- A secure lock that is tamper proof from the outside
- An RFID scanner that has the same frequency as the FU cards (13.56Mhz)
- A network connected controller that is capable of handling authentication, authorization and serving the webapplication
Possible future additions
- Authentication and authorization from other sources (LDAP/AD, centralized databases, etc)
- Centralized authentication and authorization database in case of multiple readers
- Touch screen interface to the authentication/authorization/audit-trail management application
Materials and Budget
Below are the actually required materials for the client. In agreement with Ryan we will later on add extra materials or some equipment to add to our own supply.
| Item | Links | Comments | Price (USD) | Quantity | Total |
|---|---|---|---|---|---|
| Raspberry Pi 3 or alternative controller | http://ph.rs-online.com/web/p/processor-microcontroller-development-kits/8968660/ | 40.95 | 2 | 81.90 | |
| Role of 3D printing filament | https://www.olx.ph/item/3d-printer-filaments-3-0mm-ID6NmZy.html?p=7&h=866709ada5#866709ada5 | 25.87 | 1 | 25.87 | |
| 5.1V, 1 Output, Micro USB Plug In Power Supply, 2.5A, 13W Official Raspberry Pi Power Supply | http://ph.rs-online.com/web/p/plug-in-power-supply/9098135/ | 9.63 | 2 | 19.26 | |
| RFID Reader | https://www.sparkfun.com/products/10126 | 13.56-MHz | 29.95 | 2 | 59.90 |
| Servo | https://www.sparkfun.com/products/9347 | Use the same or stronger as we have at the lab | 13.95 | 2 | 27.90 |
| Lock | Dumaguete City,Citi Hardware Store | Lock for a good quality lock, not tampering from the outside, no key outside, possible to interface with servo | 31.08 | 1 | 31.08 |
| IFixit Pro Tech Toolkit | https://www.ifixit.com/Store/Parts/Pro-Tech-Toolkit/IF145-307-1 | 110 | 1 | 110 | |
| Total USD | 356 | ||||
| Total PHP | 17166 |
Milestones
| Milestone | Title | Comments | Due date |
|---|---|---|---|
| 1. | Draft proposal | discuss and get ok from client. Include budget and planning. | |
| 2. | Final proposal | ||
| 3. | Security and privacy evaluation | All physical and electronic vulnerabilities identified and addressed | |
| 4. | RFID reader and controller design | ||
| 5. | Management application design | ||
| 6. | Testing plan | Requirements for testing the system and judge it successful | |
| 7. | First prototype | Both hardware and software developed and installed | |
| 8. | First prototype tested and design adjusted | After proper testing, adjust design according to test results | |
| 9. | Final prototype | Final prototype developed and installed | |
| 10. | Test period for final prototype completed and evaluated | After a trial period for the customer, evaluate the prototype and adjust design | |
| 11. | Final version developed and installed |
Work breakdown
Milestone 1
- Research existing (open source) tools and software for reading RFID tags
- Roughly research different protocols, standards and tools for RFID communication and authentication, resulting in a list with short description of the tools
- Research rough list of required tools and materials
- Finalize our list of requirements
- Make a material list and budget
- Make a project planning (dates on the milestones)
- Finalize this project proposal
- Discuss proposal with client
- Discuss client requirements
Milestone 2
- Adjust proposal
- Discuss proposal with client and get final OK
Milestone 3
- Evaluate potential physical attack vectors (tampering with the hardware)
- Evaluate potential local software attack vectors
- Evaluate potential remote software attack vectors
- Evaluate potential privacy flaws
- Make software security management plan (signaling and updating security updates)
Milestone 4
- Study different standards and protocols regarding RFID/NFC authentication
- Research the possibilities for the connection of the controller to the door lock
- Research different libraries for RFID-reader/controller communication
- Research different hardware components, their functioning and available libraries and tools
- Create a technical design for the RFID reader, it's controller and the lock
Milestone 5
- Research different open-source authentication and authorization packages supporting RFID
- Make a technical design of the management software
Rest:
- Get a final OK for the the designs
- Order parts
- Start writing software
- Make a software and hardware testing plan
- Install first prototype
- Train the client on use of the prototype
- Test first prototype
- Adjust design, hardware and software according to test results
- Install final prototype
- Let user evaluate the system for a while
- Evaluate the system with the user in a feedback session
- Create the final version based on the client's feedback
- Install and test the final version
Design
- RFID reader
- Controller
- Authentication and Authorization protocols and software (See also the article on Privacy Preserving Authorized RFID Authentication Protocols)
- Management webapplication
- Security and privacy
Progress
We made a 3D design for the connection between the servo and the lock, and a design for the mounting of the servo to the door. The files can be found on https://github.com/Waterspace/servo-lock-mount. If you click on the stl files, github shows you an interactive 3D view of the model.
The model has been printed, and after some tweaking, a heat gun and superglue we got it to fit! So now we need to create a casing for the electronics and hook everything up!
The code for the current arduino version can be found on github.